A vulnerability has been found in BuilderEngine, allowing the upload of a malicious file, which would result in arbitrary remote code execution.
Exploitation
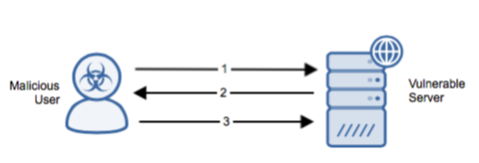
Stages
- The malicious user performs an “HTTP POST” request that includes a malicious PHP file.
- The vulnerable server responds with a successful status “HTTP 200 OK”.
- The malicious user accesses the PHP file uploaded to the server.
Prerequisites
Attack can be carried out without authentication. Attacker must be able to contact the victim host.
Vulnerability Description
A vulnerability has been found in BuilderEngine 3.5.0 via elFinder 2.0. The jquery-file-upload plugin can be abused to upload a malicious file, which would result in arbitrary remote code execution under the context of the web server.
Alert Logic Coverage
Alert Logic® has evaluated its customer base for exposure to the exploit and has developed signatures for mitigating the threat depending on the security service in place.
The Network-Based Intrusion Detection System (IDS) has been updated with the new signatures for this exploit when detected via Alert Logic Threat Manager™. If this signature is detected, an incident is generated in the Alert Logic console.
Recommendations for Mitigation
The primary mitigation strategy consists of configuring the setting on line 93 for "/themes/dashboard.assets/plugins/jQuery-File-Upload/server/php/UploadHandler.php" to accept only desired files. The example provided only allows for GIF, JPEG, and PNG files to be uploaded.
'accept_file_types' => '/\.(gif|jpe?g|png)$/i'
Furthermore, this feature should be blocked to only trusted host. In most cases, ordinary users should not be allowed to upload to the CMS. A properly configured htaccess file will provide an additional defense against this attack.
Lastly, the web server should only be allowed to execute files that are trusted or files that are located in trusted directories. If the CMS must allow for files of any type to be uploaded from untrusted users and hosts, it is mandatory that those files are never allowed to be executed.
Comments
0 comments
Please sign in to leave a comment.