An arbitrary file upload vulnerability exists in the ajax.php script used in the WordPress plugin WPShop. This vulnerability is present in versions 1.3.3.3 to 1.3.9.5. An attacker is able to upload arbitrary PHP code via crafted requests, potentially resulting in PHP code execution on the target host. No authentication is required for successful exploitation of this vulnerability.
Exploitation
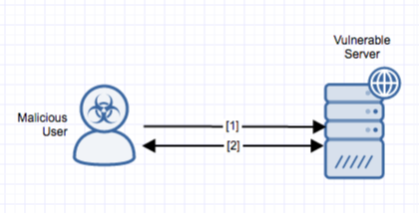
Stages
- The attacker sends an HTTP POST request to ajax.php with a malicious PHP upload contained in the POST body.
- The injected payload is processed by the target host and outputted to the WordPress uploads directory.
Prerequisites
You will need the vulnerable plugin version, in conjunction with a WordPress installation, in which the webserver has read/write permissions to the WordPress ‘uploads’ directory.
Alert Logic Coverage
Alert Logic® has evaluated its customer base for exposure to the exploit and has developed signatures for mitigating the threat depending on the security service in place.
The Network-Based Intrusion Detection System (IDS) has been updated with the new signatures for this exploit when detected via Alert Logic Threat Manager™. If this signature is detected, an incident is generated in the Alert Logic console.
Recommendations for Mitigation
Upgrade to a non-vulnerable version to mitigate this vulnerability.
Comments
0 comments
Please sign in to leave a comment.