The jQuery file upload plugin is an upload widget; it can be utilized within WordPress plugins to add upload functionality. By default, the plugin has no disallowed file types. Hence, a remote unauthenticated attacker could upload arbitrary files to the system. Due to the potential of this plugin being utilized widely in various plugins, it is beneficial to focus efforts on any potential uploads to jQuery.
Exploitation
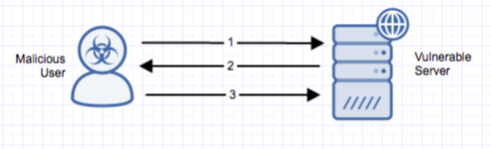
Stages
- A remote unauthenticated attacker can upload files to a server that has incorrectly configured the jQuery plugin.
- The server will respond with a JSON object indicating whether the file upload is successful.
- The attacker will be able to access their file in the predefined upload directory (user configured).
Prerequisites
The attacker will need to know if the victim has the requisite plugin installed and if it is configured to allow any file type to be uploaded.
Alert Logic Coverage
Alert Logic® has evaluated its customer base for exposure to the exploit and has developed signatures for mitigating the threat depending on the security service in place.
The Network-Based Intrusion Detection System (IDS) has been updated with the new signatures for this exploit when detected via Alert Logic Threat Manager™. If this signature is detected, an incident is generated in the Alert Logic console.
Recommendations for Mitigation
To mitigate the vulnerability, upgrade to a non-vulnerable version of the plugin.
Comments
0 comments
Please sign in to leave a comment.